NCA Challenge 2015 Progress Writeup
NOTE I was unable to complete the challenge ahead of the 18th of July deadline due to other commitments, what follows is a write up of my progress in the challenge after ~6hrs total spent.
On watching the video noted 299879 as the evidence id on the bag, this may be relevant later.
Unzip nca_image.zip
Yields nca_image.bin, let’s use binwalk to analyse the file
1 2 3 4 5 6 | |
On using binwalk -e everything except the identified QCOW image is extracted, so using my helper script
1 2 3 4 5 6 7 8 9 10 11 12 | |
We manually carve the file out
1 2 3 4 | |
Trying to analyse the QCOW file using
- guestfish
- qemu-* tools (even pulled down the latests source and compiled)
Ultimately this appears to be a false identification, opening up the file in bless noted many occurences of the QFI header associated with a qcow image, and errors such as
1 2 | |
Variant on the version of qemu being run, means I move onto analysing the rest of the extracted files.
email.docx
Opening the file (which I did on a tails VM to err on the side of caution, citing paranoia over potential for some macros), notes what appears to be a raw email complete with headers.
And an embedded oleObject
So I unzip the .dox file and again use binwalk to inspect the file.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | |
encrypted zip
binwalk has provided us with information showing this is an encrypted archive containing thress files, so its needed to extract the zip file and break the encryption to get at the files within.
1 2 3 4 5 6 7 8 9 | |
Running strings on the file also notes the following which may be of use later as it indicates the user “JAMIEH”
Z:\CSC-Final-Revision\Final ‘e-mail’\T0PS3RET.zip C:\Users\JAMIEH~1\AppData\Local\Temp\T0PS3RET.zip
Ok let’s john this bastard
1 2 3 4 | |
wav and gpg files
So now we have three files.
- fl46.wav - which upon listening to this is clearly DTMF tones followed by a modem handshake
- my_key.asc - a private GPG key
- usb_key.gpg - an encrypted GPG payload
I setup John to start brute forcing the gpg key password whilst inspecting the other files; think of it as an efficent workflow we may not need the bruteforce however there’s no harm in having it run whilst we continue the investigation
1
| |
Listening to the wav file in vlc this is clearly DTMF tones and a modem handshake, using multimon I can extract the numbers associated with the DTMF tones.
1
| |
On this first pass there is some odd behaviour occuring, some numbers are being repeated and some appear to be being skipped, opening the wav file in audacity reveals the issue.
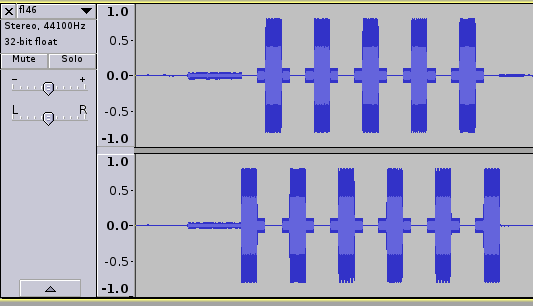
The wave file is stereo meaning there is both a left and right channel, observing the pattern above it’s clear this is an 11 didgit telephone number, we “flatten” the file to mono and run it through multimon again
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
Whilst it was not needed it’s worth noting that sox can be used to convert to a multimon native format
1
| |
Calling the number (via an anonymized service of course) yeilds a very faint voice reading numbers aloud, this is why having the call recording prior to dialing is such an advantage; some post processing to raise the volume and carefull listening yields: 533020565
usb_key.gpg
The numbers are indeed the gpg key password
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | |
Charles.pptm
2 slide presentation First slide “It is not the strongest of the species that survives, but the more adaptable”, background portrait of Charles darwin, oleEmbbeded file “TransferCode.zip.001” could infer multipart zip
1 2 3 4 5 6 7 | |
running binalk -e produxes the .zip and the .pdf file, the .pdf file is unreadable as it is incomplete therefor we know that this zip file is the head of a multipart archive.
Now I have TransferCode.zip.001
Formula.docx
Embbeded images showing a formula TransferCode.zip.002, ok yup looking like multipart zip Google image search “The Drake Equation” also “The Equation of Life” 2014 film
Found the following strings
C:\Users\Jamie H\AppData\Local\Microsoft\Windows\INetCache\Content.Word\TransferCode.zip.002 C:\Users\JAMIEH~1\AppData\Local\Temp\TransferCode.zip.002
Now I have TransferCode.zip.002
Ledger.xslx
Account numbers many 25000 transfers descriptions may be erroneous, “cabal”, “lord” etc.
Binwalk extracted noted something interesting …
./_Ledger.xlsx.extracted/secret_hash/1902d4bfb197e0b7372fc0ec592edabbce0124845a270e4508f247e1faffecce
strings ./_Ledger.xlsx.extracted/xl/embeddings/oleObject1.bin
C:\Users\Jamie H\Documents\CSCUK-Challenge-1\Stage 2\TransferCode.zip.003 C:\Users\JAMIEH~1\AppData\Local\Temp\TransferCode.zip.003
Now I have TransferCoder.zip.003
X101D4.docm
noted VBA from strings run, large binary textx (101 etc …) another hash 13790e4b2ed8345dc51b15c833aa02a33171bd839c543819d19b41bd3962943c followed by “keep looking ;-)” Used binwalk to extract the files
strings _X101D4.docm.extracted/word/vbaProject.bin
1 2 3 4 | |
the gist contains file TransferCode.zip.004 in base64encoding: https://gist.githubusercontent.com/anonymous/e13e60e1975bceb04c20/raw/145cad938bd2c4391fc55f5b482625aa86dae776/gistfile1.txt
1 2 3 4 5 6 7 8 | |
The end …
Unfortunatly this is where I must end, I originally did the above work on June 30th 2015 in my evening, and was not able to pick it up again untill autoring this blog post … past the deadline, the PDF file appears to be the final stage. (Just cat the zip files togetheer and unzip to get the PDF file)
Oh well it was an interesting puzzle at least and a welcomed exercise of skills I do not nearly get to use enough.

